Improve agent and customer experience with our new NX One. We guarantee that you will be able to unleash your Contact Center's full potential and increase contact rates by up to 100%.
All this due to our intelligent i-2CX system that increases your effective contact, which together with our NX Assurance, gives you the security to continue growing your business while complying with all regulations.
Flexibility and Trust in one place
Achieve and effective contact, complying with the NX Assurance (TCPA compliance & FDCPA 7 in 7 protection)
Exceed your customer's experience with Nuxiba.
We engineer Call Center software for the growth and development of contact and call centers

Smart Clicker?
Yes!
Our system enhance your agents to manually approve calls. It will help your CC to ensure that every contact will work with TCPA Compliance
“Stop flying solo!
Every business is like a rocket, it takes two pilots. You drive, we shotgun”.
“Stop flying solo!
Every business is like a rocket, it takes two pilots. You drive, we shotgun”.
NX One
You will have multiple communication channels from a single interface, where all system agents have access to the tool.
Access to information at all times, without installing additional components, and maintaining total control of the operation.
Each module is designed to improve your contact center and increase the estimated return on investment in less time!

So, what is NX One?
It's the perfect combination of modules, specially developed for call and contact centers.
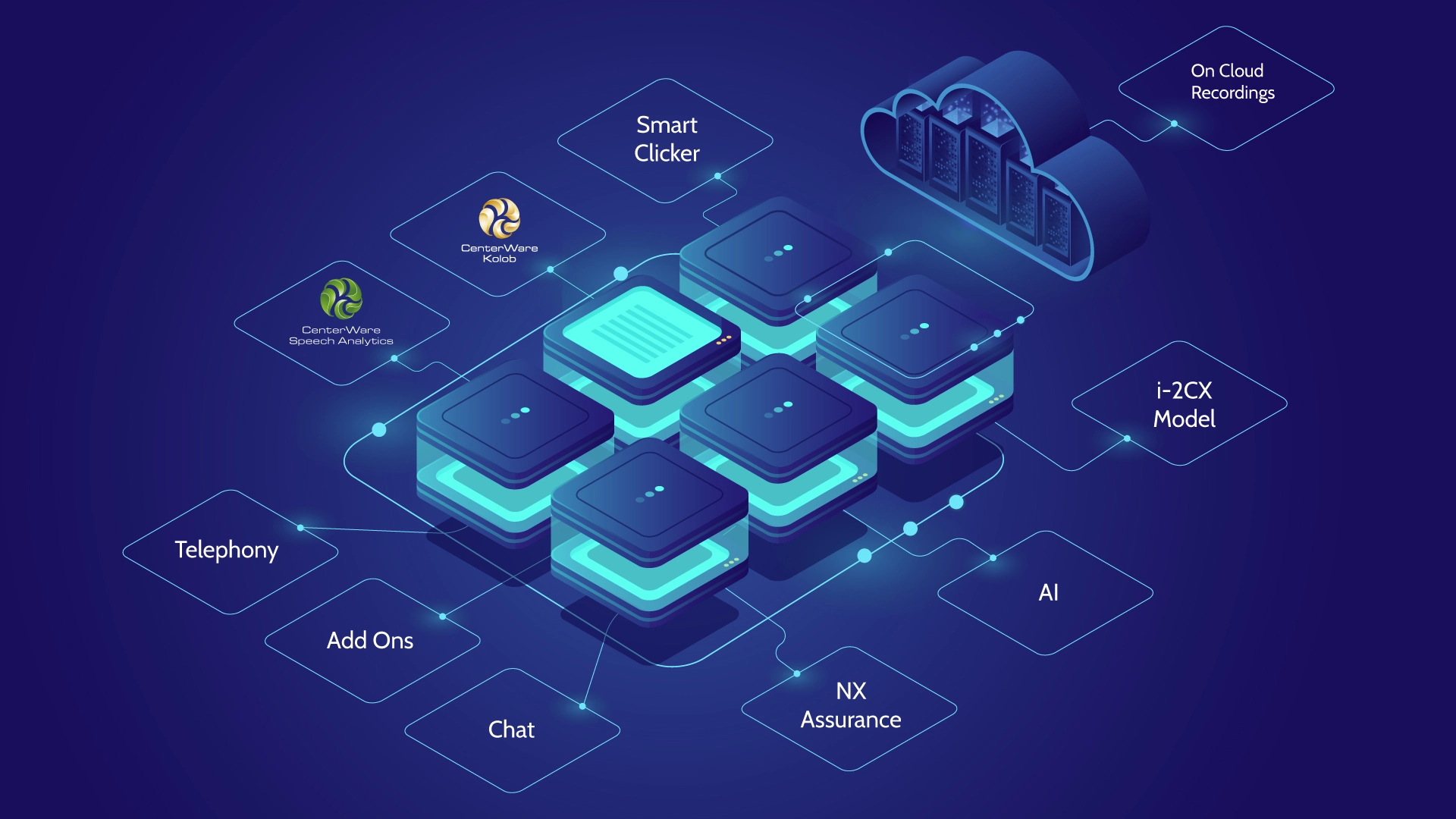
Speech Analytics
Make every word count.
AI for call center
Predict your customers' behavior and contact them.
Kolob
Upgraded and uniqueCall Center software.
Chat
Start new conversations!
Telephony
Make multiple calls at an unbeatable cost.
Disrupting technology for your Contact Center
Discover our best solutions yet
NX One
Our best solution yet for your contact and call center software.
i-2CX
The best system yet created to increase your effective contact.
NX Assurance
The perfect guarantee framework for your day to day work.

Leave your details to learn more about prices and rates.
Get in contact today with one of our specialists and let us guide you through a change into a better customer experience, collect management and sales.
Focus on what truly matters in your operations.
Let us do the hard work!
Choose between contacting us via message or book a meeting with a consultant for a better experience.


